Universal Bluetooth Gateway
for IoT based devices
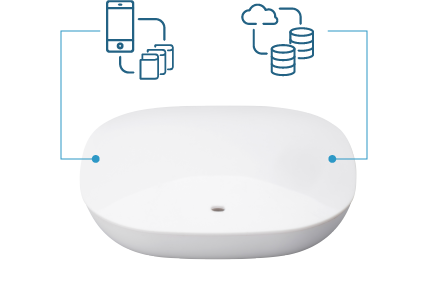
Linkk is an end-to-end solution in the form of a gateway
and cloud service that offers 100% secure connection
between local Bluetooth network and mobile device
without any risk of losing data.

How it works
Linkk provides an encrypted channel for any kind of data. Every Bluetooth Low Energy device connected to Linkk gateway can be operated via mobile application.
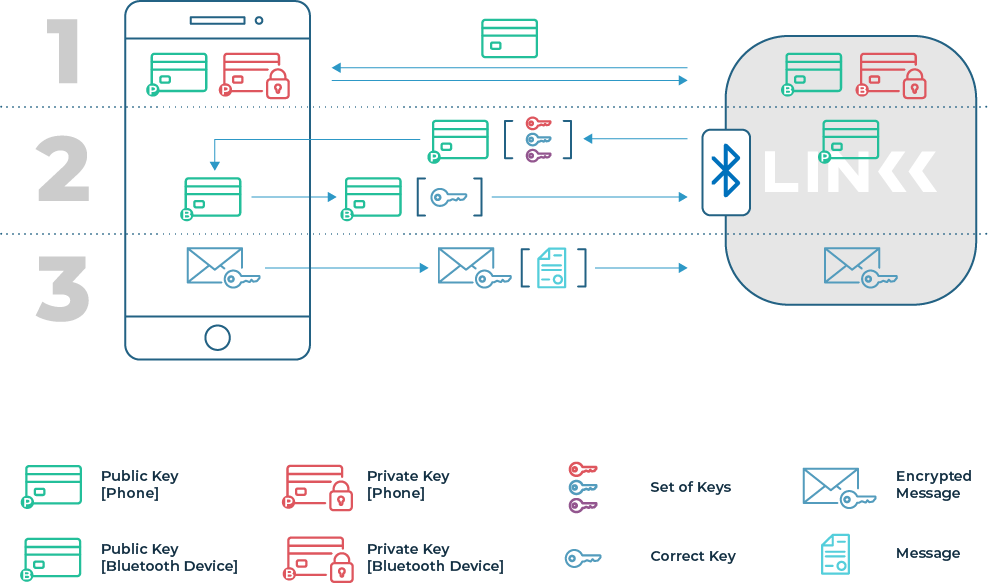
Channel encryption level is guaranteed by asymmetric cryptography that encrypts every message, in a way that can be read only by the Private Key owner. Set of Keys is generated in the provisioning process and it can only be retrived by the owner.
Features & Benefits
Hardware
(with Linux system only)

CPU:
MCIMX6G3DVM05AB

Memory / Flash:
2Gbit DDR3 128M x 16 bit
2Gbit Nand Flash
EEPROM (512 Kbit)

Reset Chip:
Equip system supervisory voltage reset with watchdog
I2C Interface:
RTC (PCF8523T/1,118)
Encryption (ATECC508A-SSHDA-B)
Hardware (with Linux system only) | Hardware |
|
|---|---|---|
 | Ready hardware + operating system |  |
 | CE and FC certificates |  |
 | Ready and tested devices with a warranty |  |
 | A possibility to order OEM products |  |
| Ready end-to-end solution |  |
|
| 100% secure tunnel-like connection |  |
|
| Easy to adapt for manufacturers |  |
|
| Modular software based on subscriber-publisher mechanisms |  |
|
| Preaggregation of data software module used to reduce cloud service data usage |  |
|
| Operating system based on Linux Yocto |  |
Technology
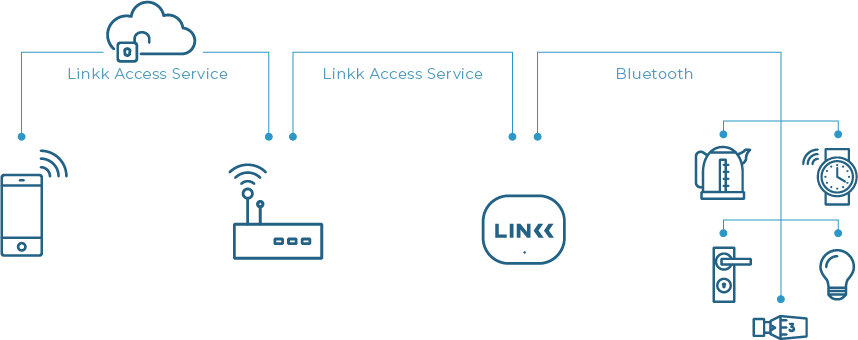
LAS - Linkk Access Service – is a set of 3 elements
Mobile app library
Data transfer system (in the cloud)
Gateway module
end2end

There is a tunnel created between Phone and Gateway, in which data is encrypted with a key determined during the provisioning process – requiring physical access to the device (gateway).
Once a key is generated, it remains in possession of the user only, and the lock for this key is only in the gateway module. As a result, the control or measurement data which passes through the system remain encrypted for the operator (Linkk), who is not able to decode them or control any of the user’s devices without their knowledge. To better explain how the system works, one can use an analogy: the system has a door map, and it knows which key fits which door without physically having any key to open it. The user has a key and a map, which allows him to open the door to which he had previously acquired the key.
asymetric crypto-solution
Pricing
Contact
Get in touch with us